Jason Voorhees
𝕸𝖊𝖗𝖈𝖊𝖓𝖆𝖗𝖞 𝕮𝖔𝖗𝖕 • 𝟐𝟎𝟐𝟒🥇
- Joined
- May 15, 2020
- Posts
- 81,503
- Reputation
- 239,388
While this forum was down I had nothing to do so this is a small write up/report that I did for master to read and then implement to ensure that this dredded screen never appears
I want to preface this by saying in not a cybersecurity expert but I do know a thing or two about keeping some malicious aliens at bay
A truly secure setup isn't about one magic bullet. So I propose creating layers of defense. If one layer fails, another catches the threat. In IT we call this "Defense in Depth"
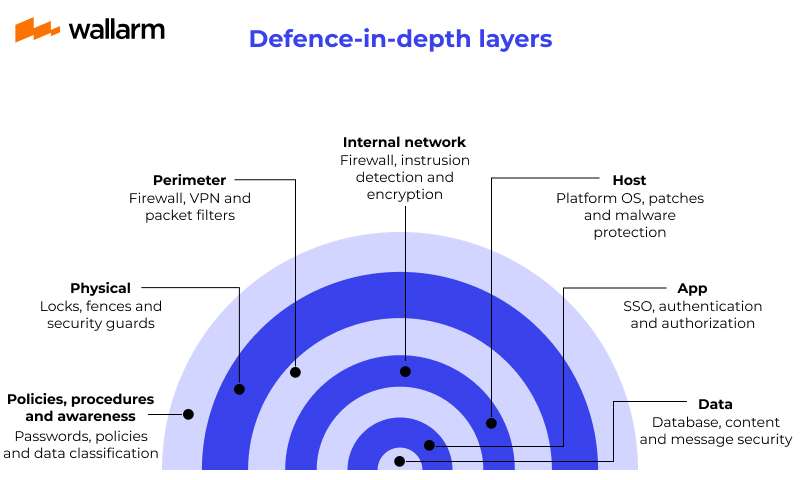
Layer 1: Rock solid Foundation (Hosting & DNS)
Get a VPS from a reputable provider. I personally recommend DigitalOcean have used it before.. They give you a clean slate and full control. You could also use Azure and AWS instances if you for some reason want even more granular control also plz no sharing of resources with incels.is keep them both seperate.
Use the "Full (Strict)" SSL/TLS mode on cloudfare
Layer 2: The Impenetrable walls
Idea is simple. Block every fucking thing and then only open the specific doors we need. It's like throwing all niggers in jail and only letting them out if they behave.
Choose any OS tbh. It doesn't matter. They are all good. Just don't use retarded legacy shit. Also use SSH Keys and disable passwords. Password logins can be bruteforced. Keys cannot also an important lesson that I learn is changing the port. Many bots scan port 22 the default all day looking for a loophole. Change it to something else.
The VPS provider already has a cloud firewall just use that but I also suggest to add one on the server too with iptables. Only allow incoming traffic on ports 80 and 443 ( and only from Cloudflare's IP Ranges. They can't hit what they can't see.
Install Fail2Ban. The automated watch dog that scans logs for repeated failed logins and exploit scanning and automatically blocks the offending IPs immediately. The gold standard. I am linking the GitHub Link

 github.com
github.com
Do the above and you've already eliminated 99% of automated attacks but we are not done yet when I said this forum isn't going down. I mean it.
Layer 3: The Ever watching Gatekeeper
User Ngnix with PHP-FPM. This is something I learnt recently so I am linking the article just configure it to run PHP processes as non privileged user
 www.digitalocean.com
www.digitalocean.com
Generate a SSL certificate on your server. I like to use this one because it's free

This is for encrypting traffic between Cloudflare and your server ensuring there are no weak links in the chain.
The final guardian-Authenticated Origin Pulls. Many people will say this is overkill but who tf cares. We have need extreme security because we looksmaxers are all at danger due to trannies on IT always trying to ruin our lives
What is basically does is creates a cryptographic handshake that proves a request is coming from Cloudflare. If an attacker discovers your real server IP, they still can't access your website because their requests won't have the secret handshake.
AOP doesn't stop DDOS style volume attacks so you need network-level defenses for that built-in DDoS protection is good enough but I suggest Magic Transit. It is again overkill for a forum and the standard ddos protection is more than good enough but we are building for an end of the world scenario so you might aswell throw this in.
Generally good practices/advice
-Always run the latest stable version of XenForo and your add-ons
-Require Two Factor Authentication for all admin and moderator accounts. This is already being done I think but this is a must. A stolen password should not be enough to compromise the forum
-Every add-on is a potential security hole so vet them regularly for bug/vulnerabilities. Only install reputed ones
-Your last line of defense is a good backup. If the worst happens and all the IT trannies takeover the forum. You can wipe the server and restore from a known good state. Just run a script to perform a SQL dump daily or weekly basis , send it to Amazon S3 with versioning and in the takeover scenario. Wipe everything and do a rollback to start new.

I want to preface this by saying in not a cybersecurity expert but I do know a thing or two about keeping some malicious aliens at bay
A truly secure setup isn't about one magic bullet. So I propose creating layers of defense. If one layer fails, another catches the threat. In IT we call this "Defense in Depth"

Layer 1: Rock solid Foundation (Hosting & DNS)
Get a VPS from a reputable provider. I personally recommend DigitalOcean have used it before.. They give you a clean slate and full control. You could also use Azure and AWS instances if you for some reason want even more granular control also plz no sharing of resources with incels.is keep them both seperate.
Use the "Full (Strict)" SSL/TLS mode on cloudfare
Layer 2: The Impenetrable walls
Idea is simple. Block every fucking thing and then only open the specific doors we need. It's like throwing all niggers in jail and only letting them out if they behave.
Choose any OS tbh. It doesn't matter. They are all good. Just don't use retarded legacy shit. Also use SSH Keys and disable passwords. Password logins can be bruteforced. Keys cannot also an important lesson that I learn is changing the port. Many bots scan port 22 the default all day looking for a loophole. Change it to something else.
The VPS provider already has a cloud firewall just use that but I also suggest to add one on the server too with iptables. Only allow incoming traffic on ports 80 and 443 ( and only from Cloudflare's IP Ranges. They can't hit what they can't see.
Install Fail2Ban. The automated watch dog that scans logs for repeated failed logins and exploit scanning and automatically blocks the offending IPs immediately. The gold standard. I am linking the GitHub Link
GitHub - fail2ban/fail2ban: Daemon to ban hosts that cause multiple authentication errors
Daemon to ban hosts that cause multiple authentication errors - fail2ban/fail2ban
Do the above and you've already eliminated 99% of automated attacks but we are not done yet when I said this forum isn't going down. I mean it.
Layer 3: The Ever watching Gatekeeper
User Ngnix with PHP-FPM. This is something I learnt recently so I am linking the article just configure it to run PHP processes as non privileged user
How to Configure PHP-FPM with NGINX for Secure PHP Processing | DigitalOcean
Learn how to configure PHP-FPM with NGINX for efficient, secure PHP execution. Explore installation, setup, and performance tuning best practices.
 www.digitalocean.com
www.digitalocean.com
Generate a SSL certificate on your server. I like to use this one because it's free

Let's Encrypt
Let's Encrypt is a free, automated, and open Certificate Authority brought to you by the nonprofit Internet Security Research Group (ISRG). Read all about our nonprofit work this year in our 2025 Annual Report.
letsencrypt.org
This is for encrypting traffic between Cloudflare and your server ensuring there are no weak links in the chain.
The final guardian-Authenticated Origin Pulls. Many people will say this is overkill but who tf cares. We have need extreme security because we looksmaxers are all at danger due to trannies on IT always trying to ruin our lives
What is basically does is creates a cryptographic handshake that proves a request is coming from Cloudflare. If an attacker discovers your real server IP, they still can't access your website because their requests won't have the secret handshake.
AOP doesn't stop DDOS style volume attacks so you need network-level defenses for that built-in DDoS protection is good enough but I suggest Magic Transit. It is again overkill for a forum and the standard ddos protection is more than good enough but we are building for an end of the world scenario so you might aswell throw this in.
Generally good practices/advice
-Always run the latest stable version of XenForo and your add-ons
-Require Two Factor Authentication for all admin and moderator accounts. This is already being done I think but this is a must. A stolen password should not be enough to compromise the forum
-Every add-on is a potential security hole so vet them regularly for bug/vulnerabilities. Only install reputed ones
-Your last line of defense is a good backup. If the worst happens and all the IT trannies takeover the forum. You can wipe the server and restore from a known good state. Just run a script to perform a SQL dump daily or weekly basis , send it to Amazon S3 with versioning and in the takeover scenario. Wipe everything and do a rollback to start new.
Last edited: