Jason Voorhees
Say cheese
- Joined
- May 15, 2020
- Posts
- 79,934
- Reputation
- 233,425
As you nighas know I’ve been dipping my feet into cybersec for a few days.

 looksmax.org
looksmax.org
So yesterday I decided to set up an isolated test lab in Oracle VirtualBox and spun up a Windows 10 retail ISO image to do some authorized testing but even with aggressive scans and deep fingerprinting I couldn’t find shit. 0 vulnerabilities
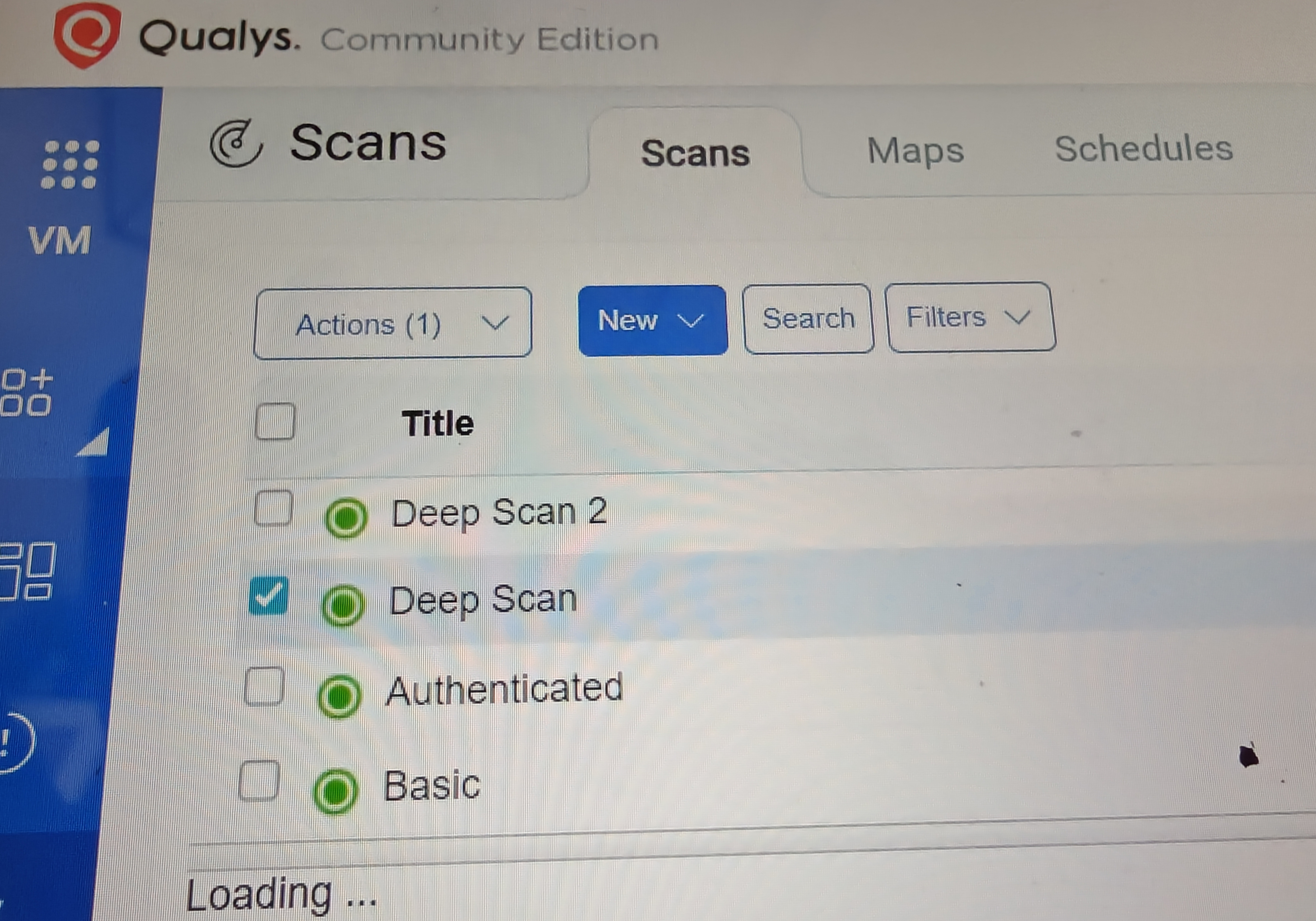
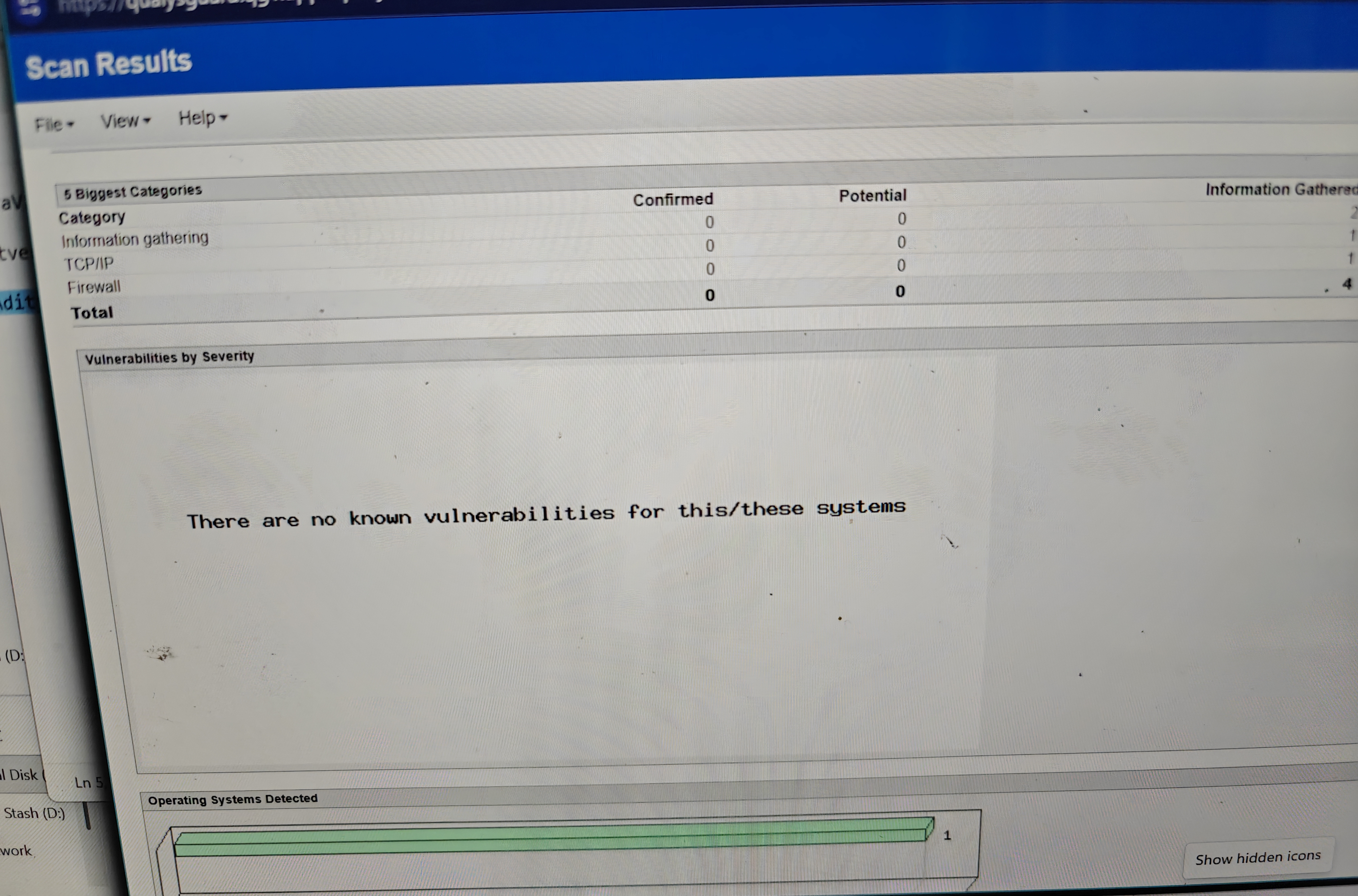
Nmap TCP/UDP sweeps, vulnerability scanners and web fuzzing against services you name it and it all just returned noise.
I swapped the guest to a Windows 10 Insider (beta) build and things finally opened up but not in the easy CTF way I expected. The behavior I found was a mess. Fragile chains, timing sensitive race conditions, and misconfigurations that only show up under certain driver states. I used packet captures and found weird kernel mode driver failures also with noisy Windows Defender/IDS alerts and a thicket of mitigation technologies ASLR, DEP, UAC prompts, Credential Guard all fighting me at once and at the same time.
In plain English it wasn't like a simple hole in the wall that I could just punch through and bulldoze inside like I was used to. It was more like a fortress with tiny invisible cracks and trying to pick locks while the door and locks kept changing shape and location. Every time thought I had a weak spot. Windows moved the goalpost
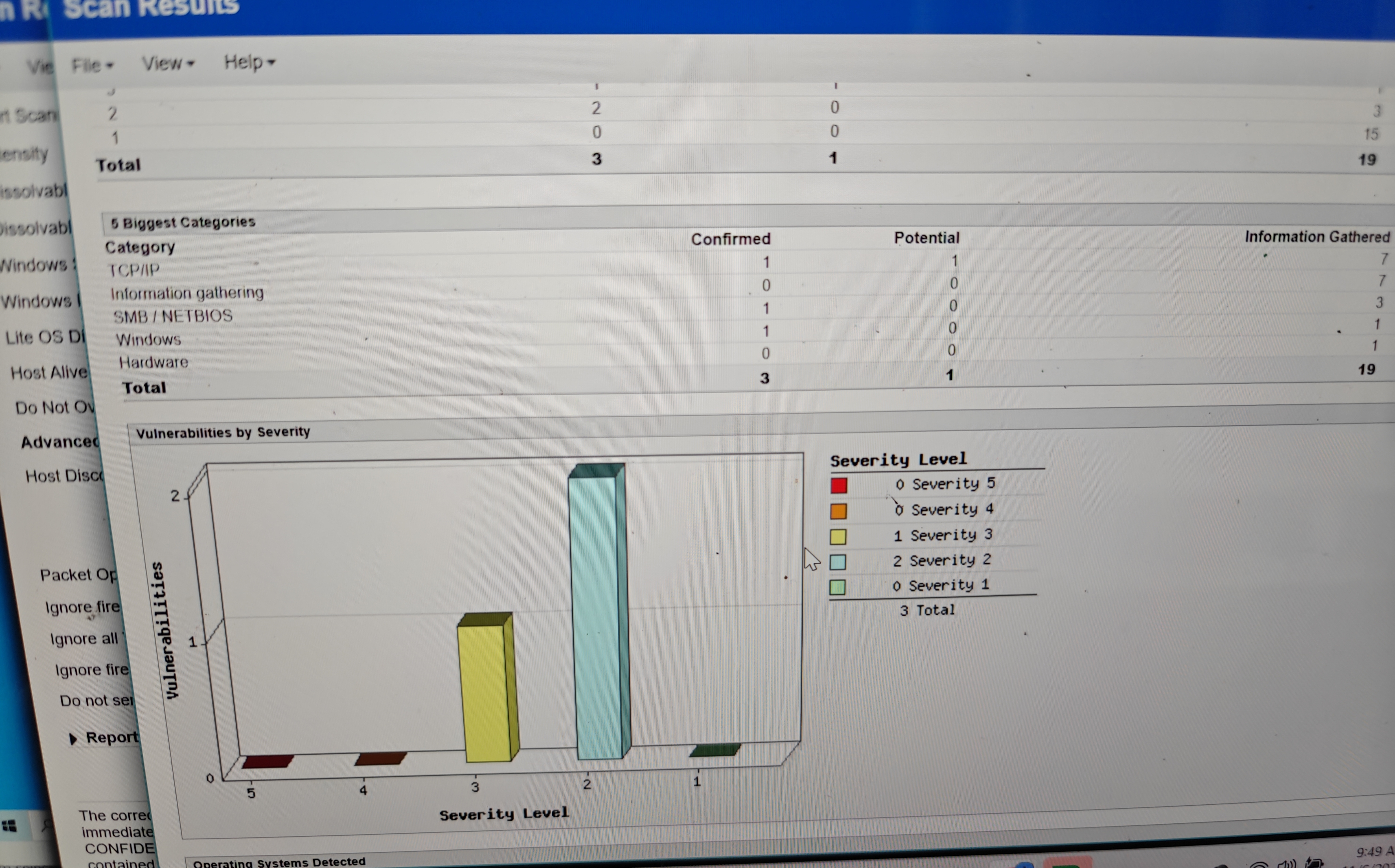
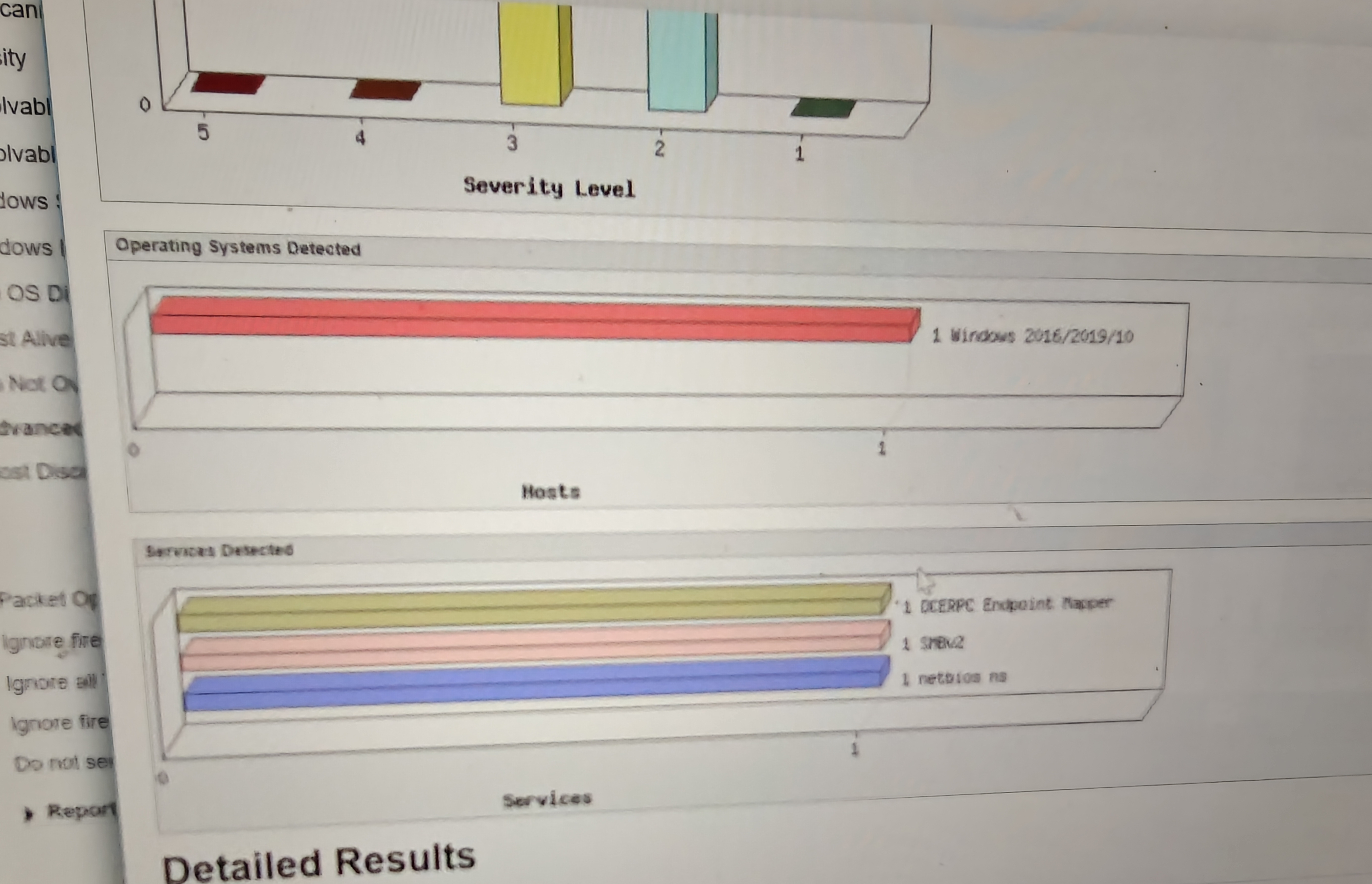
The exploit paths weren’t one shot easy exploits. They required careful carefully crafted payloads. Every test run triggered alerts Windows Event Viewer spiked with Process Creation and AppLocker hits and the IDS flagged all the suspicious flows. I probably set off a hundred alarms across.At this point I was so deep I stopped noticing time.
My girlfriend walked in saw me clenching my fists over a frozen terminal, and laughed why are you so angry at random pixels? She told me come let's go out to have some ice cream and tried to drag me away I told her I wasn’t leaving the chair until I finished. She sighed and said ah so its one of those days where you turn into a lunatic satisfying your ego. All right good luck and left me to it.
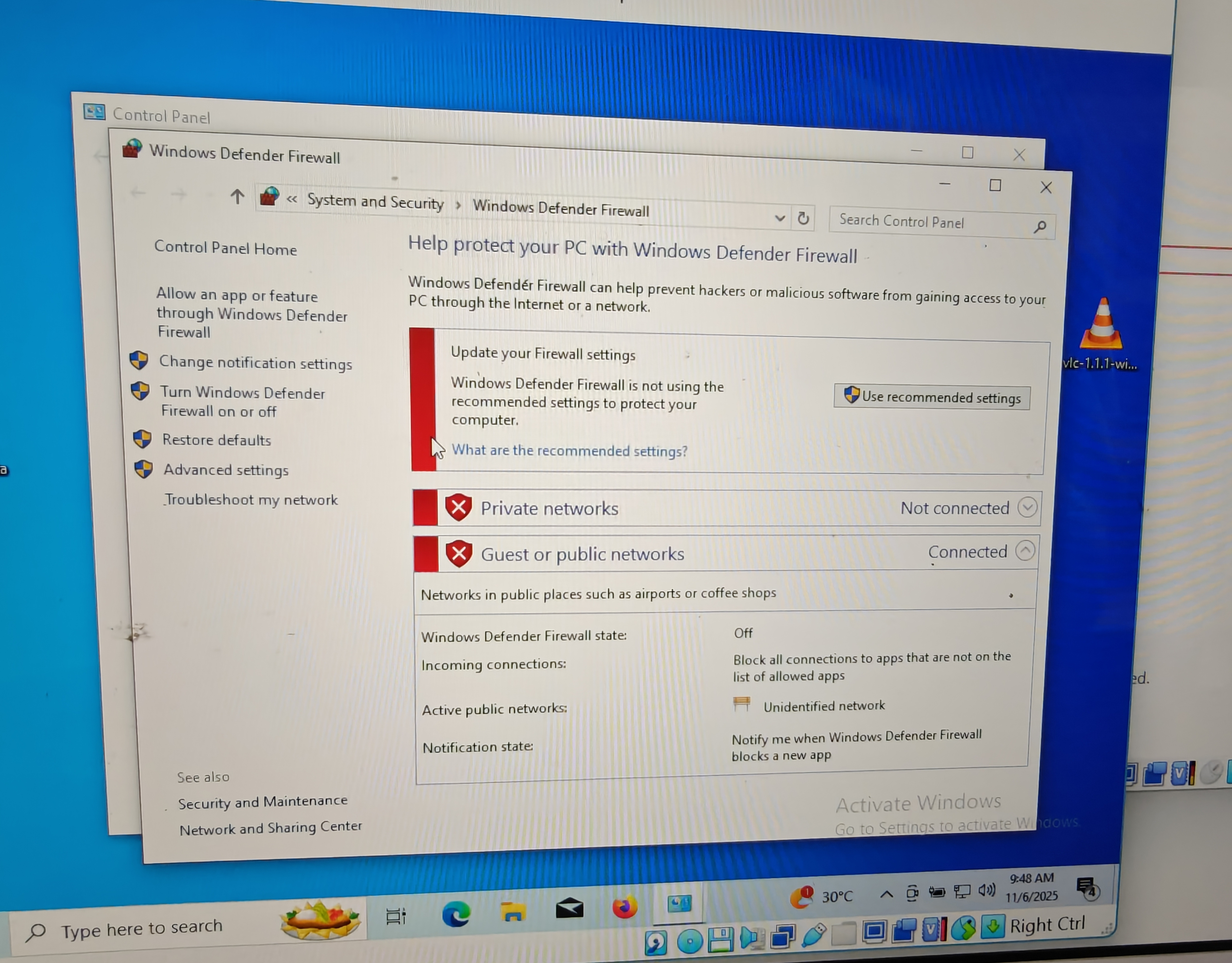
Every time I tried to do something even minor Windows Defender + Event Viewer + AppLocker would collectively come in to rape me and fuck everything up ruining all progress. Five hours of digging, iterating, and re imaging and scouring the internet to find known exploits and workarounds later replaying packet sequences individually and using logs from Procmon and Wireshark I finally saw the behavior I wanted and started dismantling it and finally managed to disable the windows defender firewall proof above and got elevated shell like response and a clean set of artifacts in the logs that proved the chain had worked. Literally hours of wrestling with the defenses, insane frustration, hundreds of alarms all for a small, fragile minor win. Nigga I finna cry. Fucking hell. I'm going to sleep and won't touch my computer for a few hours. Fuck this shit.

What I learned: Modern Windows is a fortress of layered defenses that turns exploitation into a grueling marathon of plumbing logs correlating events.
As an amateur I came away humbled. Even after knowing about the exploits and Internet helping me all throughout it was nightmare to do it. Windows security and constant updates that it asks are isn't the pain in the ass they are designed to be extremely robust and resilient. It makes attackers fight tooth and nail for every inch. The real weakest link. Isn't the system security. Microsoft has built a beast of a setup it's your dumbass that clicks on random shit that makes it vulnerable not the Operating System.

I am learning cybersecurity now
I never get tired of learning This guy's YouTube channel is really good https://youtube.com/@kevingaray_cyberguy My goal is to learn all these tools in the next 2-3 months
So yesterday I decided to set up an isolated test lab in Oracle VirtualBox and spun up a Windows 10 retail ISO image to do some authorized testing but even with aggressive scans and deep fingerprinting I couldn’t find shit. 0 vulnerabilities


Nmap TCP/UDP sweeps, vulnerability scanners and web fuzzing against services you name it and it all just returned noise.
I swapped the guest to a Windows 10 Insider (beta) build and things finally opened up but not in the easy CTF way I expected. The behavior I found was a mess. Fragile chains, timing sensitive race conditions, and misconfigurations that only show up under certain driver states. I used packet captures and found weird kernel mode driver failures also with noisy Windows Defender/IDS alerts and a thicket of mitigation technologies ASLR, DEP, UAC prompts, Credential Guard all fighting me at once and at the same time.
In plain English it wasn't like a simple hole in the wall that I could just punch through and bulldoze inside like I was used to. It was more like a fortress with tiny invisible cracks and trying to pick locks while the door and locks kept changing shape and location. Every time thought I had a weak spot. Windows moved the goalpost


The exploit paths weren’t one shot easy exploits. They required careful carefully crafted payloads. Every test run triggered alerts Windows Event Viewer spiked with Process Creation and AppLocker hits and the IDS flagged all the suspicious flows. I probably set off a hundred alarms across.At this point I was so deep I stopped noticing time.
My girlfriend walked in saw me clenching my fists over a frozen terminal, and laughed why are you so angry at random pixels? She told me come let's go out to have some ice cream and tried to drag me away I told her I wasn’t leaving the chair until I finished. She sighed and said ah so its one of those days where you turn into a lunatic satisfying your ego. All right good luck and left me to it.

Every time I tried to do something even minor Windows Defender + Event Viewer + AppLocker would collectively come in to rape me and fuck everything up ruining all progress. Five hours of digging, iterating, and re imaging and scouring the internet to find known exploits and workarounds later replaying packet sequences individually and using logs from Procmon and Wireshark I finally saw the behavior I wanted and started dismantling it and finally managed to disable the windows defender firewall proof above and got elevated shell like response and a clean set of artifacts in the logs that proved the chain had worked. Literally hours of wrestling with the defenses, insane frustration, hundreds of alarms all for a small, fragile minor win. Nigga I finna cry. Fucking hell. I'm going to sleep and won't touch my computer for a few hours. Fuck this shit.

What I learned: Modern Windows is a fortress of layered defenses that turns exploitation into a grueling marathon of plumbing logs correlating events.
As an amateur I came away humbled. Even after knowing about the exploits and Internet helping me all throughout it was nightmare to do it. Windows security and constant updates that it asks are isn't the pain in the ass they are designed to be extremely robust and resilient. It makes attackers fight tooth and nail for every inch. The real weakest link. Isn't the system security. Microsoft has built a beast of a setup it's your dumbass that clicks on random shit that makes it vulnerable not the Operating System.
Last edited: